TryHackMe: The Great Disappearing Act
A detailed walkthrough of the CTF challenge, covering reconnaissance, enumeration, exploitation, and privilege escalation.

A detailed walkthrough of the CTF challenge, covering reconnaissance, enumeration, exploitation, and privilege escalation.

medium-rated
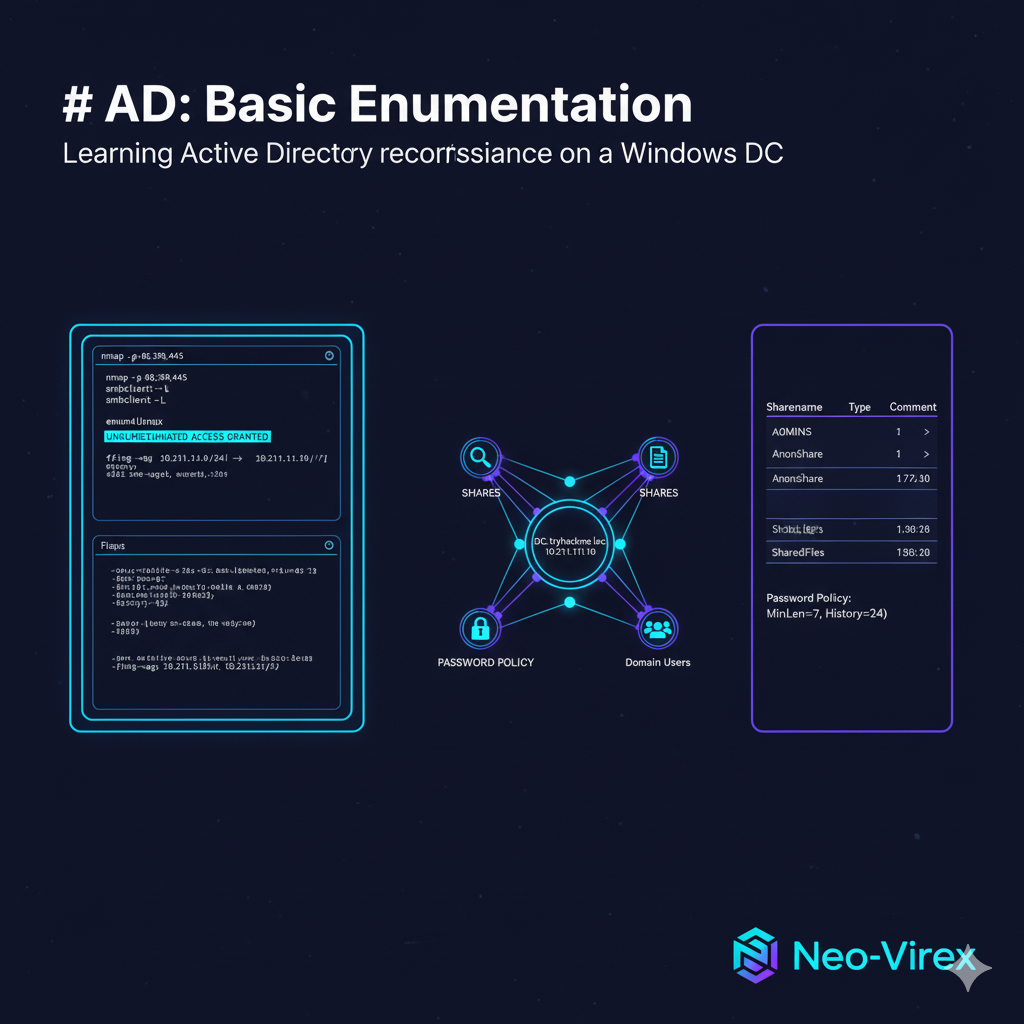
Learning Active Directory reconnaissance on a Windows DC (TryHackMe-style)

a medium-rated TryHackMe room that focuses on exploiting vulnerabilities in a site and performing privilege escalation to obtain the flag.
Never tell me the odds.
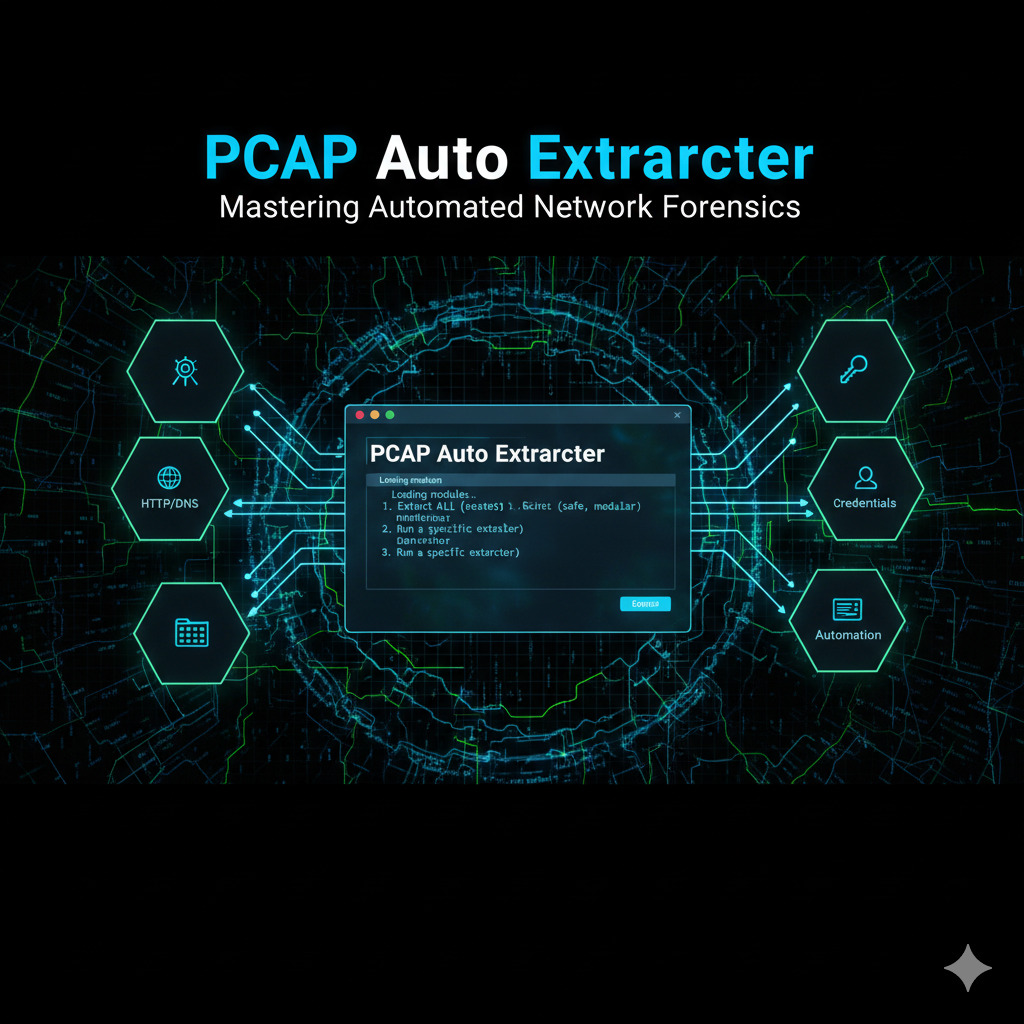
Network forensics is a critical component of cybersecurity investigations, enabling analysts to uncover malicious activities, understand attack patterns, and gather evidence.

Windows privilege escalation (priv-esc) covers elevating a local account to Administrator/SYSTEM, and leveraging that foothold to gain higher privileges in Active Directory.

Windows privilege escalation (priv-esc) covers both elevating a local user account to Administrator/SYSTEM on a host, and then leveraging that foothold to compromise higher privileges in an Active Directory domain..

This write-up documents a complete walkthrough of the Biohazard CTF challenge. It integrates the detailed steps from the reference HTML write-up (originally from the Bio-hazard TryHackMe page) with my own investigation, notes, and captured artifacts. It explores each phase in sequence reconnaissance, enumeration, exploitation, and **privilege escalation alongside captured flags, passwords, tools, and decryption paths.

A comprehensive Capture The Flag (CTF) challenge series named “BUNNA”, designed with realistic network segmentation, progressive narrative, and layered technical puzzles covering steganography, web exploitation, privilege escalation, and more